Cryptolocker [DANGER]
-
Dear All,
The following was recently circulated by our IT department.
"Please be very vigilant regarding the Cryptolocker ransomware that is currently in circulation. This particular malware, if opened, will silently encrypt files on a Windows PC, and on any network drive that you can write to. It then attempts to extort hundreds of dollars in return for an unlock key. The University IT Services strongly advise that you should not pay the ransom (there is no guarantee that these crooks will actually release your files even if you do pay).
At present Cryptolocker’s main vector appears to be e-mail, pretending to be a ‘voice mail’ attachment, but there are also reports of infections spreading via Word or Excel files received by email, or even in shared Dropbox folders. A number of variants have come to light over the last couple of days, and it may adopt further vectors in the next few days. If you believe that you have been affected, please let us know immediately, but please appreciate that we will not be able to recover any files that have been encrypted by Cryptolocker. We may be able to help by restoring files from backups but this may not help with files you have been actively working on. Also backups may be overwritten with encrypted versions of the files if you don’t let us know quickly. If you are managing your own windows based system/laptop please check that your regular backups are completing properly.
Our anti-malware measures have identified and removed dozens of examples of Cryptolocker in the last few days but there is no guarantee that it won't appear in a form that slips through. So please do not open unexpected attachments received by email, particularly if they claim to be voice mail messages from systems you’ve never heard of, or from people you do not know.
You can find out more at e.g. http://en.wikipedia.org/wiki/CryptoLocker"
Also this http://www.youtube.com/watch?v=Gz2kmmsMpMI
Regards,
Bob -
thanks!
@unknownuser said:
The most widespread variants of the Cryptolocker malware are detected by Kaspersky products with the following verdicts:
Trojan-Ransom.Win32.Blocker.cfkz, Trojan-Ransom.Win32.Blocker.cmkv, Trojan-Ransom.Win32.Blocker.cggx, Trojan-Ransom.Win32.Blocker.cfow, Trojan-Ransom.Win32.Blocker.cjzj, Trojan-Ransom.Win32.Blocker.cgmz, Trojan-Ransom.Win32.Blocker.cguo, Trojan-Ransom.Win32.Blocker.cfwh, Trojan-Ransom.Win32.Blocker.cllo, Trojan-Ransom.Win32.Blocker.coew."
To manually prevent the infection:
You need to prevent the execution of files from:
%appdata%
%localappdata%
%temp%
%UserProfile%
compressed archiveYou can set software restriction policies:
http://technet.microsoft.com/en-us/library...1(v=ws.10.aspx
http://support.microsoft.com/kb/310791Kaspersky Support Forum
Kaspersky forum where Kaspersky product users and experts share tips, advice, help and solutions in your preferred language

Kaspersky Support Forum (forum.kaspersky.com)
-
Thanks Bob, made the post a sticky.
-
Fortunately virus-writers rarely 'support' the MAC OS

-
Yep
-
The Physics department at Oxford is taking this threat really seriously. Apart from implementing various measures, they also recommending that people consult this guide:
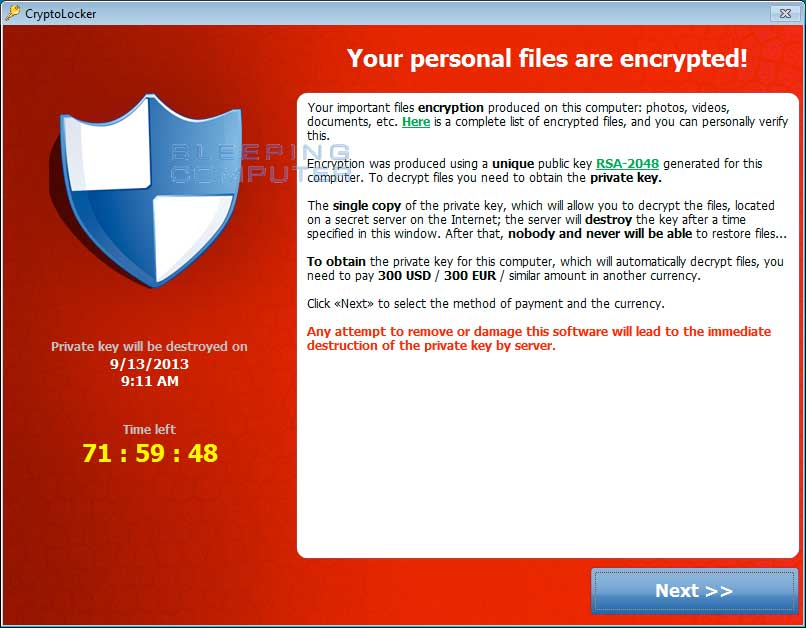
CryptoLocker Ransomware Information Guide and FAQ
This guide provides information and answers to frequently asked questions regarding the CryptoLocker ransomware. It provides a break down of what this infection does, how it encrypts your data, and how you can possibly restore your files.
BleepingComputer (www.bleepingcomputer.com)
Hope this helps everyone to understand the threat, and how to avoid being caught out.
The key advice seems to be 'back up all your files', and preferably on removable storage.
Kind regards,
Bob -

CryptoLocker Is The Nastiest Malware Ever & Here's What You Can Do
CryptoLocker is a type of malicious software that renders your computer entirely unusable by encrypting all of your files. It then demands monetary payment before access to your computer is returned.

MUO (www.makeuseof.com)
-
It happened yesterday to one of the businesses in my building.
He appears to have an inadequate backup system and uses a free version of Antivirus software.
He is now paying the ultimate penalty as he appears to have lost about 80% of his files (and still counting)
-
Wow! That's pretty crazy.
-
yeh it certainly is Rich
The guy is a Civil Engineer, in his early to mid 30's....a fit and healthy looking bloke, until now.
He is devastated, and looks quite ill.
-
More info here:
http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware/
http://krebsonsecurity.com/2013/11/cryptolocker-crew-ratchets-up-the-ransom/As always - remote backups are absolutely critical if you are running a business. Not using Windows can also be helpful

-
@unknownuser said:
Not using Windows can also be helpful

I'm guessing once Apple becomes a real contender with a fair amount of users it will be a target also, right now they do not have enough users to warrant the effort.
-
Our offices and staff have used windows to defend windows (seems simple doesn't it?) for the past 8 years. Since we kicked out the third parties (security experts..lol) there have been no issues at all. There are two groups of people having issues with windows security, people who don't use windows, and people who use it and insist on using products other than those developed by windows to maintain it.
-
"http://www.bleepingcomputer.com/"
I went there and I would recommend that you stay away from the site. Like many stories of virus devastation this one is really riddled with bull. The site has some focused obsession with malware. If you run into a room full of people trading "torrents" and talking about security it is best to back out of the room.
-
This forum post is going on three years old now...that's pretty hot...
 I guess modeling has become a business for very serious people. No time for frivolity.
I guess modeling has become a business for very serious people. No time for frivolity. 
-
@roland joseph said:
This forum post is going on three years old now...that's pretty hot...
 I guess modeling has become a business for very serious people. No time for frivolity.
I guess modeling has become a business for very serious people. No time for frivolity. 
wait, what's wrong with frivolity? Are you trying to encourage it by posting in an old thread?

Advertisement







